PowerDNS is an open-source Domain Name System (DNS) server. You can use this service as a DNS server, for hosts and services on your local network.
Note that PowerDNS requires the PostgreSQL service to store DNS data. For instructions on adding a PostgreSQL instance, see PostgreSQL.
Add a PowerDNS instance
- In the Secure Edge Portal, navigate to Marketplace > Service Listing and select PowerDNS.
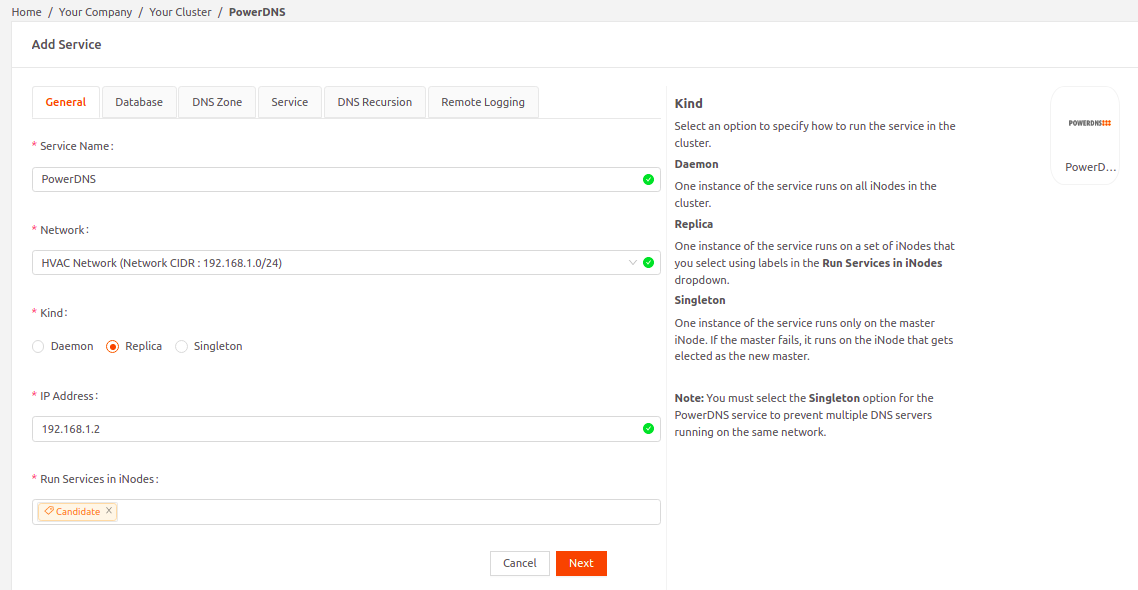
- Enter a name for the service instance, and select the network for this instance.
- Specify a static IP Address for this service instance. It should belong to the same subnet as the local network CIDR, but must be outside the DHCP range. For example, if your local network uses 10.10.0.0/24, and the DHCP range is 10.10.0.15 - 10.10.0.253, select a static IP address from the range 10.10.0.1 - 10.10.0.14.
- The Kind field is visible only if you're adding the service to a cluster. Specify how to run the service in the cluster:
- Daemon: One instance of the service runs on all nodes in the cluster.
- Singleton: One instance of the service runs only on the master node, or the newly elected master if the original fails.
- Replica: Choose this option to ensure that an instance of PowerDNS is running on all candidate nodes in the cluster, which reduces DNS downtime during failovers. If you select this option, in the Run Services in Nodes dropdown menu, select the label Candidate. (The Secure Edge Portal automatically adds this label to all candidate nodes for you.)
- Continue to the Database tab. Specify the following:
- PostgreSQL Service IP Address: The IP address of the PostgreSQL service for PowerDNS to access its database. PowerDNS service requires the PostgreSQL service to store DNS data.
- Database Name: The name of the PostgreSQL database that PowerDNS will use.
- User Name: The user name that PowerDNS will use to access its PostgreSQL database.
- Password: The password that PowerDNS will use to access its PostgreSQL database.The Database Name, User Name, and Password settings must match the corresponding PostgreSQL configuration.
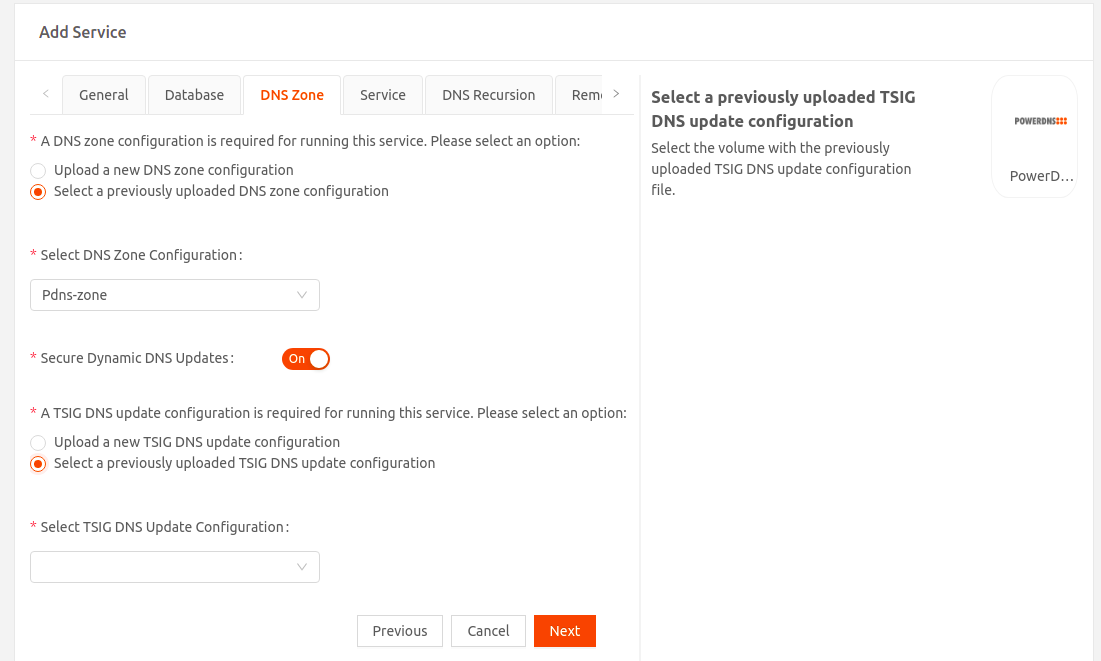
- Continue to the DNS Zone tab and upload either a new or previously used configuration. The DNS zone file extension must be .zone.
- Enable Secure Dynamic DNS Updates if you want to secure dynamic DNS updates using TSIG keys. Upload either a new or previously used configuration. The TSIG DNS update configuration file must be .conf.ImportantThe TSIG key name in the TSIG DNS update configuration file must match the corresponding key name in the Kea DDNS configuration file.
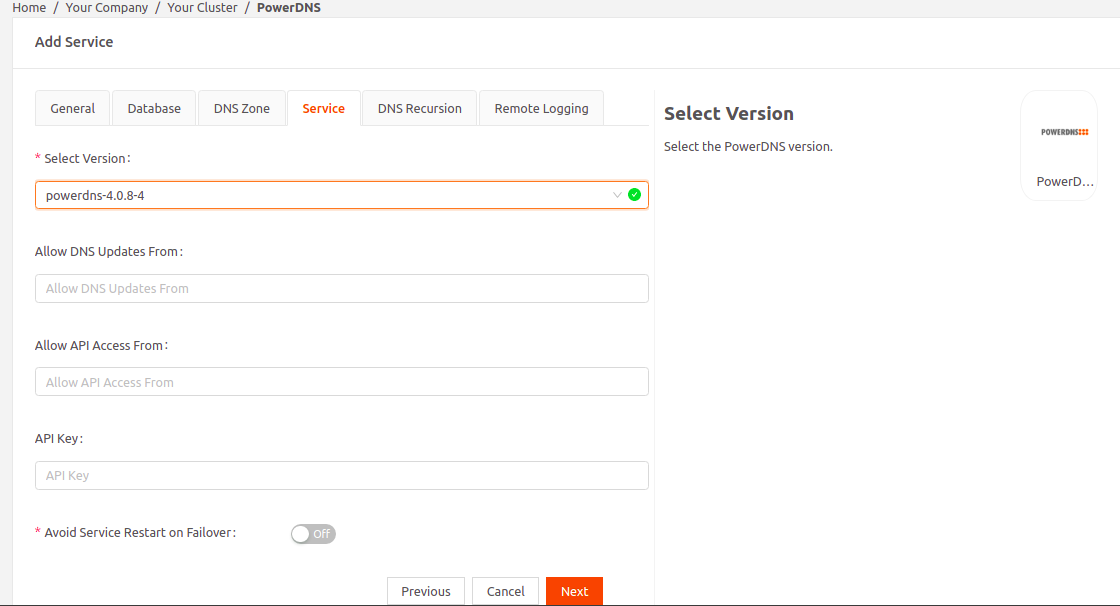
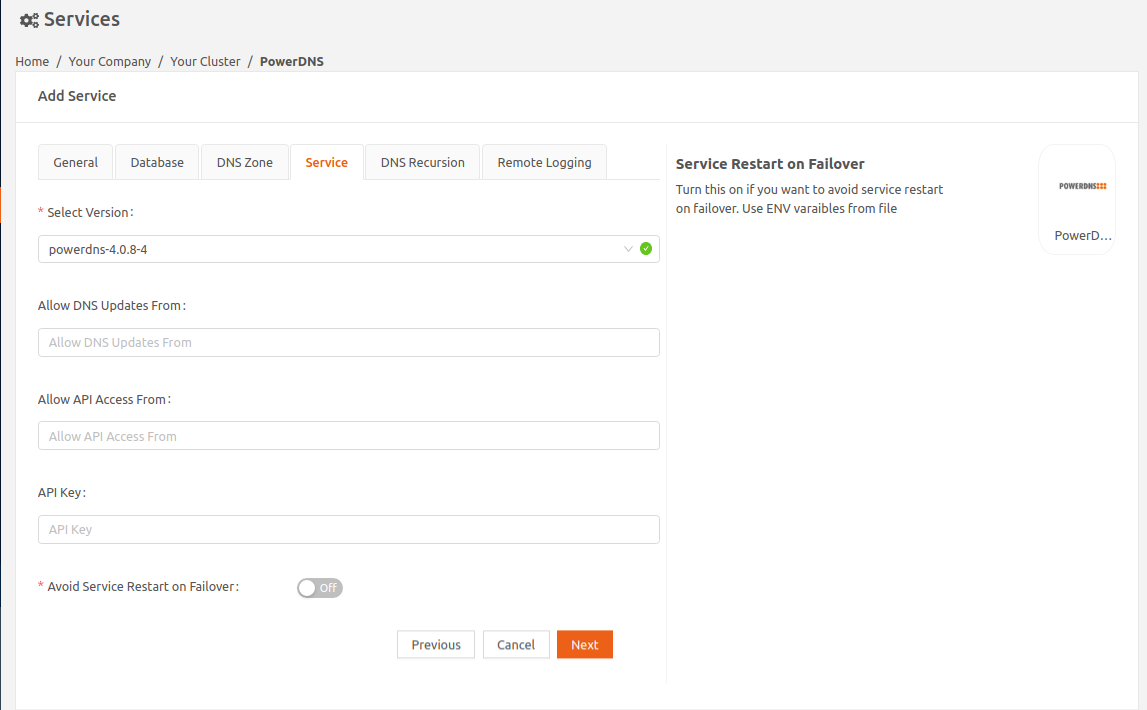
- Continue to the Servicetab and select the PowerDNS image version.NoteWith PowerDNS version 4.5.4-1, the authoritative and the recursor part of PowerDNS runs as two separate containers within the same service.PowerDNS authoritative service used for Dynamic DNS updates listens on port 5300. PowerDNS recursor service used for Recursive queries listens on port 53.
- To dynamically update DNS data, in the Allow DNS Updates From field, specify a comma separated list of IP addresses or ranges (in CIDR format) that are allowed to perform DNS updates. By default, dynamic DNS updates are not allowed from any host.To allow the Kea service to dynamically update DNS mapping based on DHCP lease change events, configure the Kea DDNS server and specify the IP address of the Kea service here.
- If you want to provide access to specific hosts, in the Allow API Access From field, specify a comma separated list of IP addresses or ranges (in CIDR format) that are allowed to access the API. By default, API access is restricted to the local host.
- In the API Key field, set the static pre-shared authentication key that hosts need to use to access the API.
- To avoid service restart on cluster master failover, enable the Avoid Service Restart On Failure option.
- Choose the custom DNS server option.
- Set the PowerDNS service IP address as the DNS server IP address.Set the DNS Server IP address to the PowerDNS service IP address. This ensures that across the failovers, the DNS IP address for the postgres service remains the same, and the service mode seamlessly switches from backup to master without any service restart.
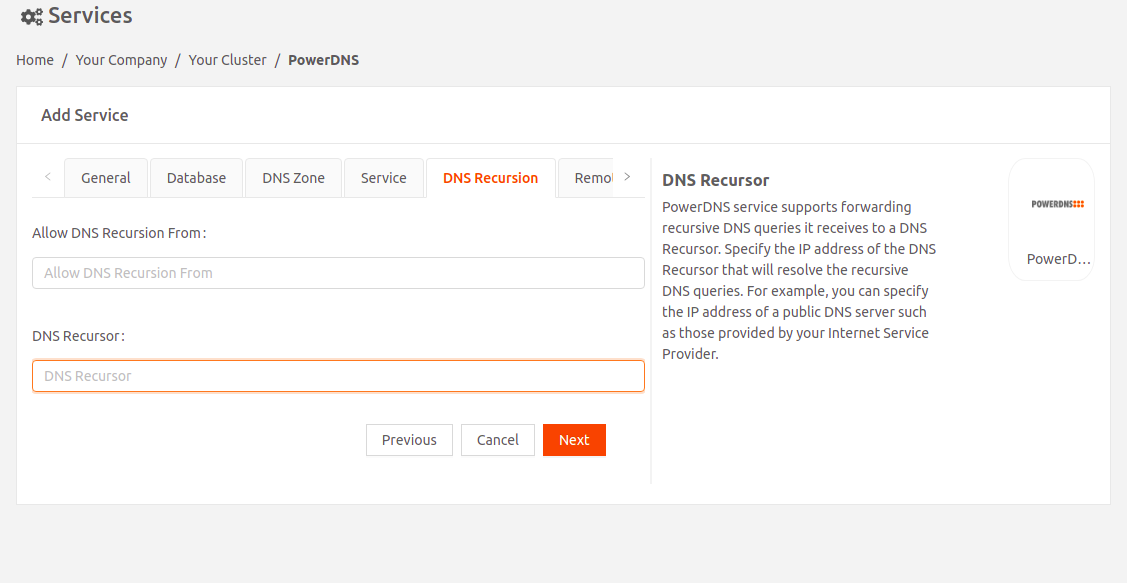
- Continue to the DNS Recursion tab. This is an optional configuration to forward DNS queries unresolved by this PowerDNS service to a Recursor (another DNS server that can resolve these queries).
- Allow DNS Recursion From: To allow recursive queries to specific hosts, specify a comma-separated list of IP address ranges (in CIDR format) that are allowed to perform recursive DNS queries. By default, recursive queries are restricted to the local host.
- DNS Recursor: PowerDNS service supports forwarding recursive DNS queries it receives to a DNS Recursor. Specify the IP address of the DNS Recursor, for example, a public DNS server provided by your Internet Service Provider.
 On PowerDNS version 4.5.4-1, the recursor server runs as a separate container and listens on port 53 within the PowerDNS service.
On PowerDNS version 4.5.4-1, the recursor server runs as a separate container and listens on port 53 within the PowerDNS service.
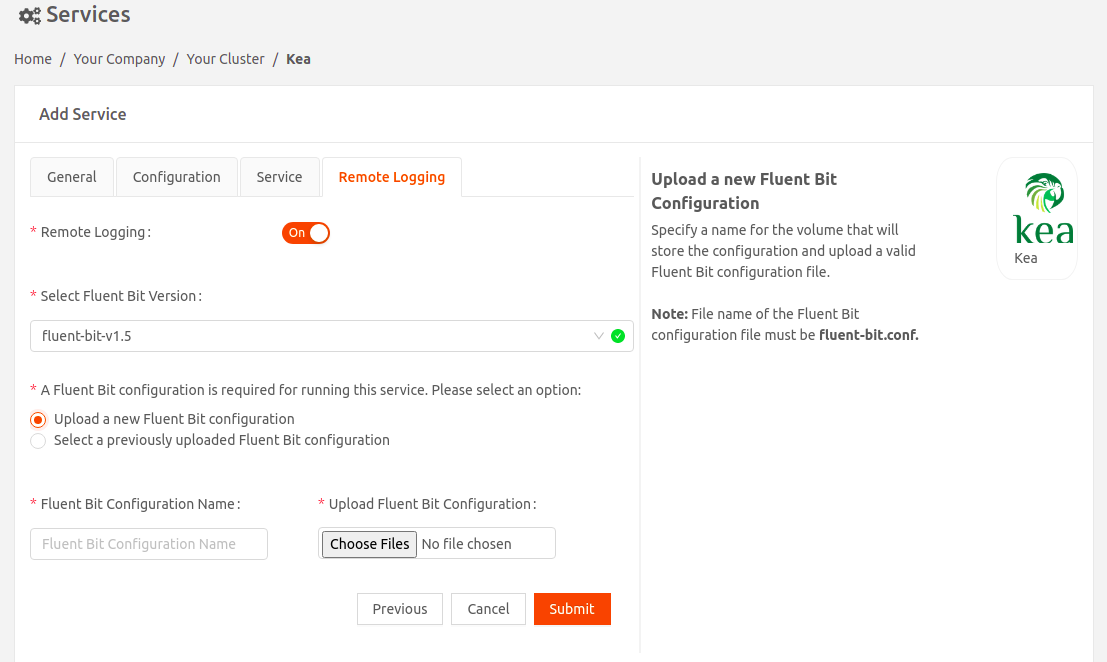
- Continue to the Remote Logging tab. Enable Remote Logging if you want to send service logs to a remote destination of your choice using Fluent Bit, an open-source log processor and forwarder.
- Select Fluent Bit Version: Select the Fluent Bit image version.
- Upload either a new Fluent Bit configuration or a previously uploaded one.ImportantThe Fluent Bit configuration filename must be fluent-bit.conf.
- Select Submit to finalize your changes.
PowerDNS version notes
Image version pdns-4.0.8-4 and zone files
(Image tag: iotium/powerdns:4.0.8-4-amd64)
This PowerDNS image supports reloading of edited zone files. You can now edit and reload your zone files for existing zones with pre-seeded contents. If you are updating an existing secret, please restart the PowerDNS container for the new secret content (zone files) to take effect. Images prior to pdns-4.0.8-4 do not support zone-file updates.
The default behavior for the following settings has been changed:
- Allow DNS Recursion From: By default, the access is restricted to local host on image iotium/powerdns:4.0.8-4-amd64. This is a change from previous images where, by default, the access was open to all.
- Allow API Access From: By default, the access is restricted to local host on image iotium/powerdns:4.0.8-4-amd64. This is a change from previous images where, by default, the access was open to all.
Migrate an existing deployment to pdns-4.0.8-4
To use the PowerDNS image supporting the zone edits, you can migrate from pdns-4.0.8-3 to pdns-4.0.8-4 image version in the Service→Image Version drop-down and update the existing service. Make sure that you update the image to the latest version, and then try updating the zone files.
Image version powerdns-4.5.4-1
(Image tag: iotium/powerdns:4.5.4-1amd64)
This version has been released as powerdns 4.0.8 is now at end-of-life (eol). PowerDNS version 4.5.4-1 has two containers:
- Authoritative server — The powerdns 4.5.4 authoritative server is used for dynamic DNS updates and it listens on port 5300. Make sure to configure the Kea-dhcp-ddns config file to update the DNS server for this port.
- Recursive server — The powerdns 4.5.8 recursive server is used for handling DNS queries and it listens on port 53.
Migrate an existing deployment to powerdns-4.5.4-1
To use the powerdns-4.5.4-1 image, from the Service > Select Version dropdown, select the new image and update the existing service.